Cyber Trust
-research and development project
by Karo Saharinen
Institute of Information Technology
JAMK University of Applied Sciences
karo.saharinen@jamk.fi
(Use the Space key or Swipe to navigate through the slides.)
SDN Architecture 1.0
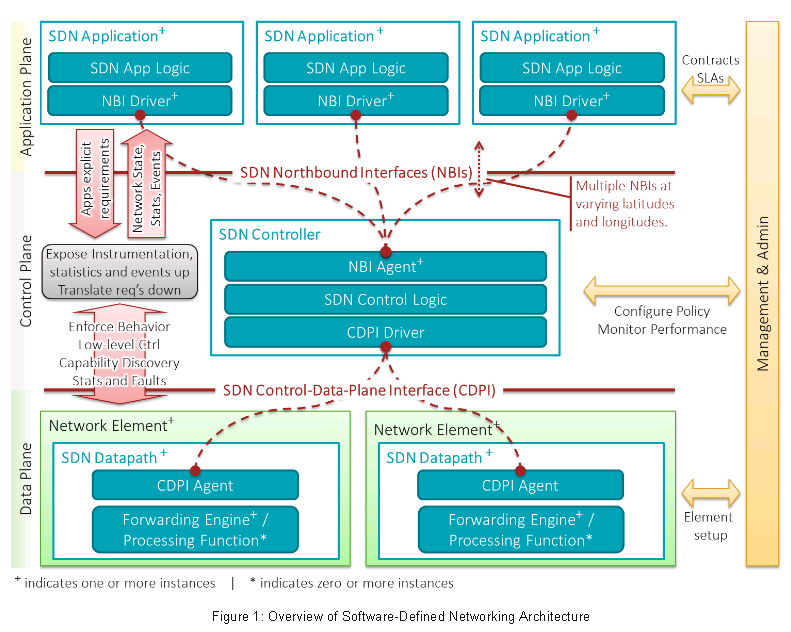
Source: ONF: SDN Architecture 1.0
SDN Architecture 1.1
This SDN architecture issue 1.1 is a stand-alone document that clarifies and extends issue 1, but does not render it obsolete.
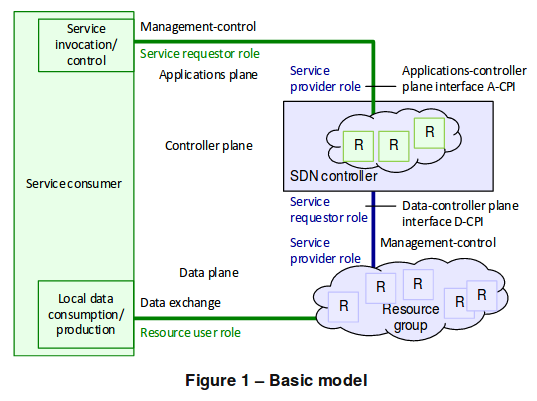
Source: ONF: SDN Architecture 1.1
SDN on Gartner Hype Cycle, 2015
Network and Communications
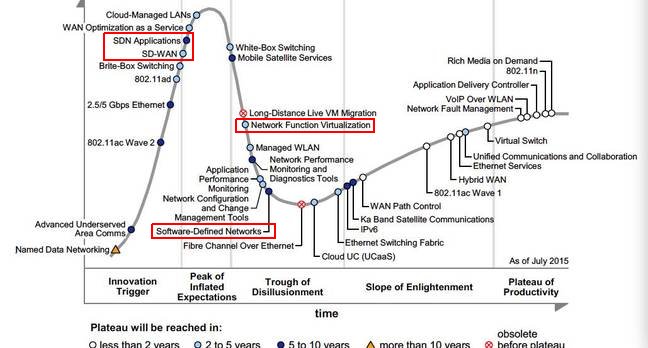
SDN on Gartner Hype Cycle, 2015
Network and Communications
“During 2015, we started to see production adoption of SDN solutions, though broad deployments are still relatively rare. A variety of both established vendors and startups continue to develop SDN technologies, but full, robust, end-to-end enterprise-ready solutions are not yet fully established on the market.”
Source: http://blogs.gartner.com/andrew-lerner/2016/07/28/networking-hype-cycle-2016/
SDN on Gartner Hype Cycle, 2016
Emerging Technologies
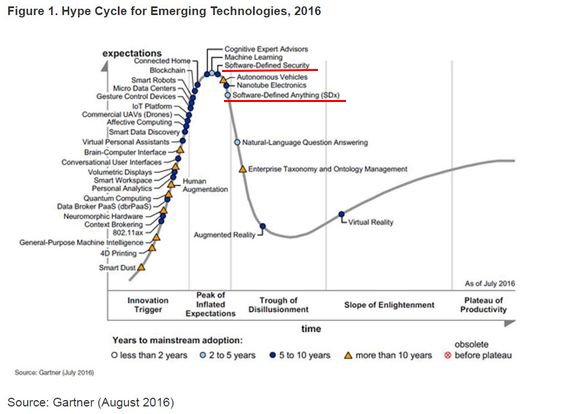
Source: http://www.tivi.fi/Kaikki_uutiset/sdsec-ohjelmisto-ohjaus-tulee-tietoturvaan-6604647 & Gartner
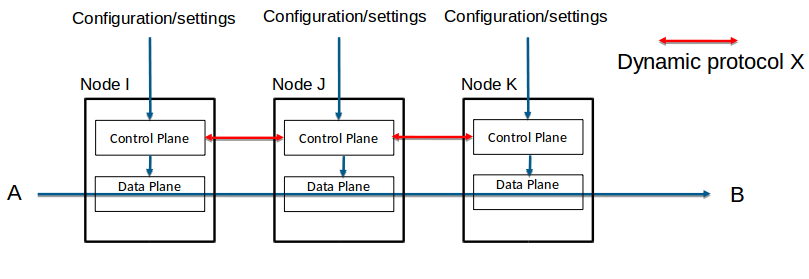
Networking - The "old way"
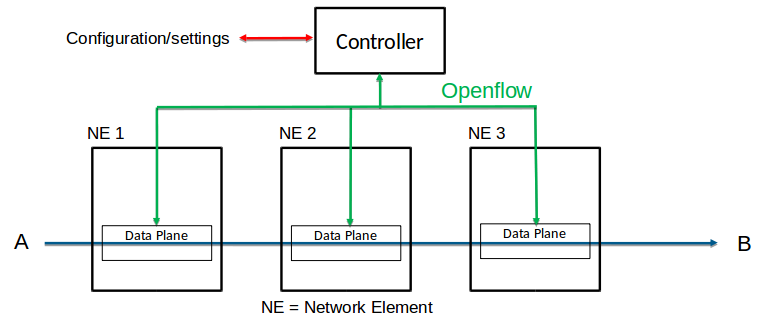
Networking - The "SDN way"
Cyber Trust
DIMECC Program:
We Return the Trust to the Digital World
- DIMECC stands for Digital, Internet, Materials & Engineering Co-Creation.
- DIMECC is the leading breakthrough-oriented co-creation ecosystem that speeds up time to market. Our innovation platform makes leaders and winners meet. Our network consists of 2.000+ R&D&I professionals, 400+ organizations, 69 shareholders and 10+ co-creation facilitators.
Cyber Trust
Research Themes
- Secure Services
- Securing Platforms and Networks (<- JAMK)
- Security and reliability of modern distributed information systems depends critically on both mobile and cloud computing platforms and on the communication networks that connect them.
- Similarly, the communication networks need to be designed to be resilient under continuous attacks and to provide safe, isolated environments for critical functions and applications.
- Advanced Threats and Security Assurance
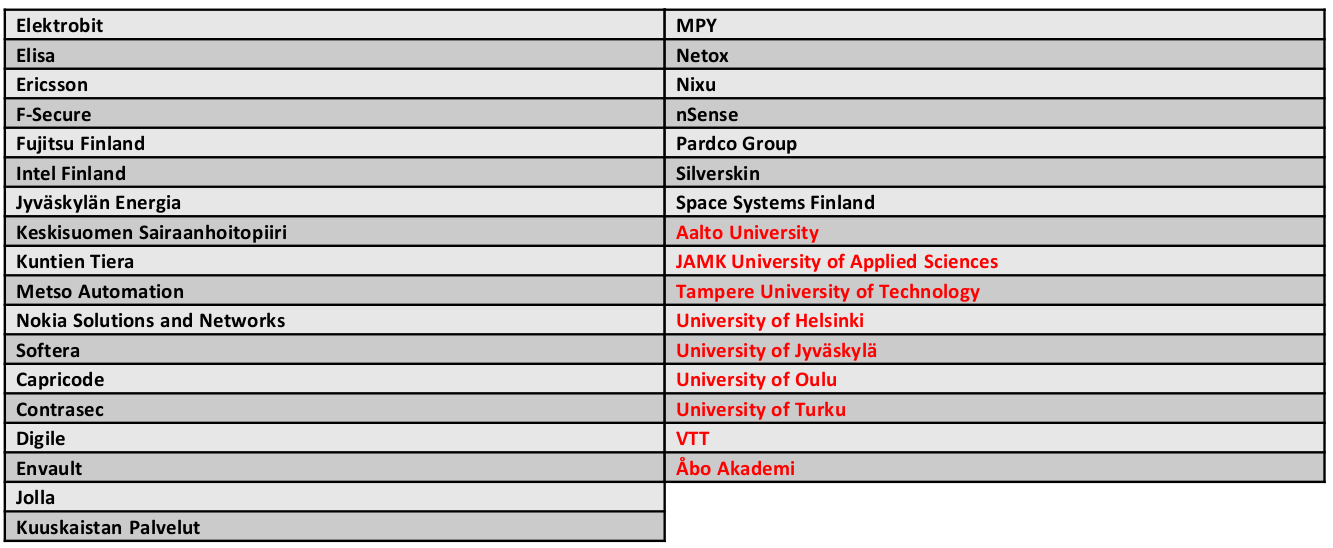
Cyber Trust
Project members
Cyber Trust
Project lifecycle
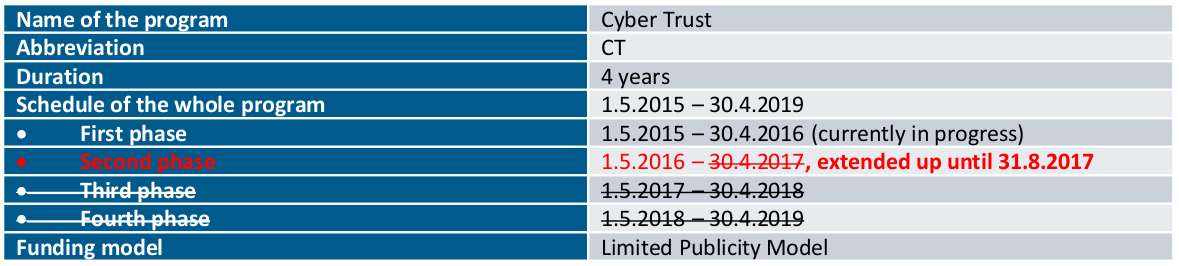
Cyber Trust
Work Packages
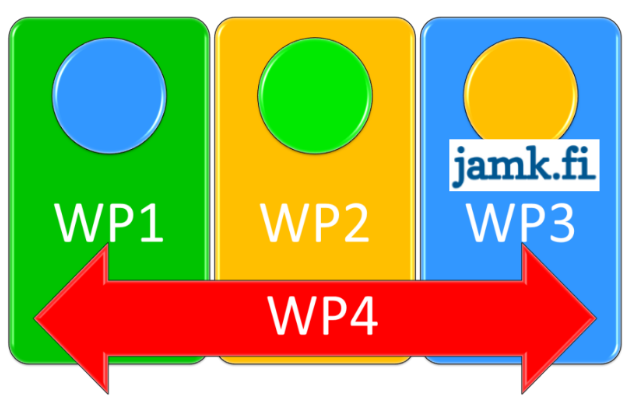
- WP0: Program Management
- The main objective is to steer the Program and dissemination to enable the sharing of achievements, experiences, successes and difficulties for the benefit of the Finnish cyber security community.
- WP1: Secure Services
- The ultimate goal is to provide secure and cost efficient Cloud security model where privacy, identity and resiliency issues are considered
- WP2: Secure Platforms
- The objective of this WP is to focus on platform-level security as a whole: from the underlying hardware, up to the software, through to the architecture
- WP3: Security in New Network Technologies
- The objective of the work in this work package is to get a clearer picture of the security-related threats and opportunities in future network and communication technologies.
- WP4: Advanced Threats and Security Assurance
- The main objective of this work package activities is to study key threats across societies and economies, design effective methods and tools for detecting and countering those, and validate such methods and tools via modern security assurance techniques and in practical testing.
Cyber Trust
Work Packages
- We are participating in Work Package 3 (WP3) and the Cyber Trust Case:
- Goal 1: Implement a SDN testbed based on expected business opportunities with related elements and interfaces for prototyping future systems. Identify missing security components.
- Goal 2: Based on research literature, existing technologies and the SDN testbed, investigate potential NFV architectures and it’s security improvements on top of it and their business models. Identify business critical key architectures and key areas to investigate further (see task 2).
- Goal 3: Study, investigate and identify the cyber threats and attack models and vectors of the selected key architectures (see task 3).
- Building on the above results and findings, the tentative goals of the later phases of the project are:
- Goal 4: Study, investigate and identify the protection techniques and models for these new interfaces and elements of in a flexible network architecture (see task 4 - Secure network management).
- Goal 5: Investigate the security technology for SDN and NFV architectures for new use cases (see task 7).
- Goal 6: Develop mechanism for implementing domain isolation in a multi-tenant environment (see task 5).
- Goal 7: Identify means for service chaining, i.e. how to integrate network services (FW, AAA, IDS) into SDN. Develop means for handling service chaining in the presence of increased end-to-end (e2e) encryption of user plane traffic (see task 6).
- Goal 8: Understand the cyber business consequences and opportunities for value creation and capture related to SDN based new Internet architecture (see task 8).
Cyber Trust
Related to Other DIMECC projects
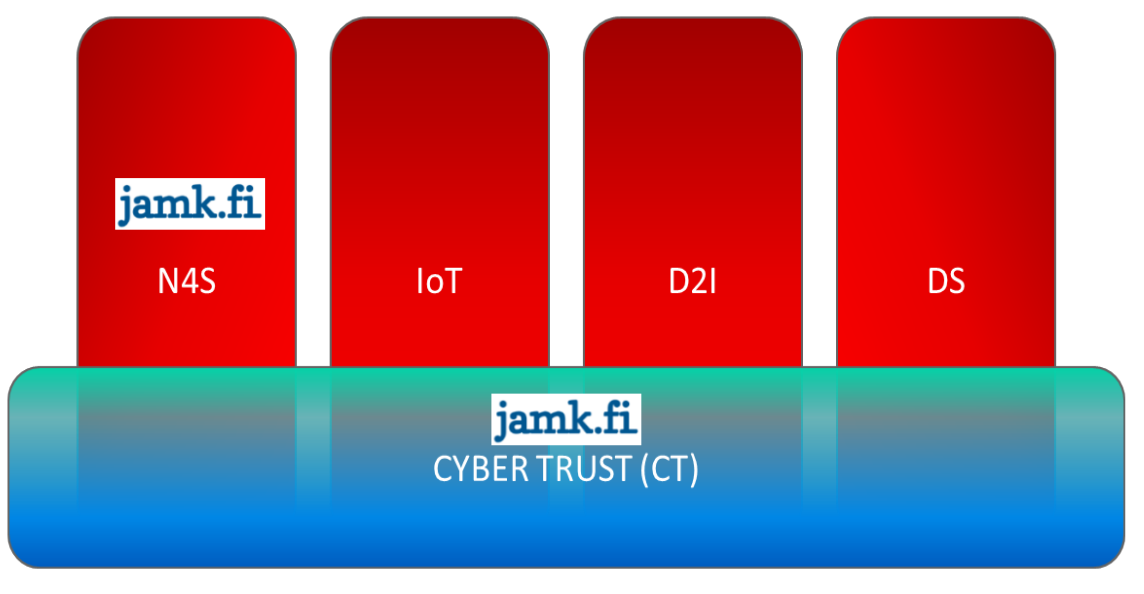
- Cyber Trust connects to other programs funded by DIMECC as seen in the picture
Cyber Trust
SDN Testbed for researchers
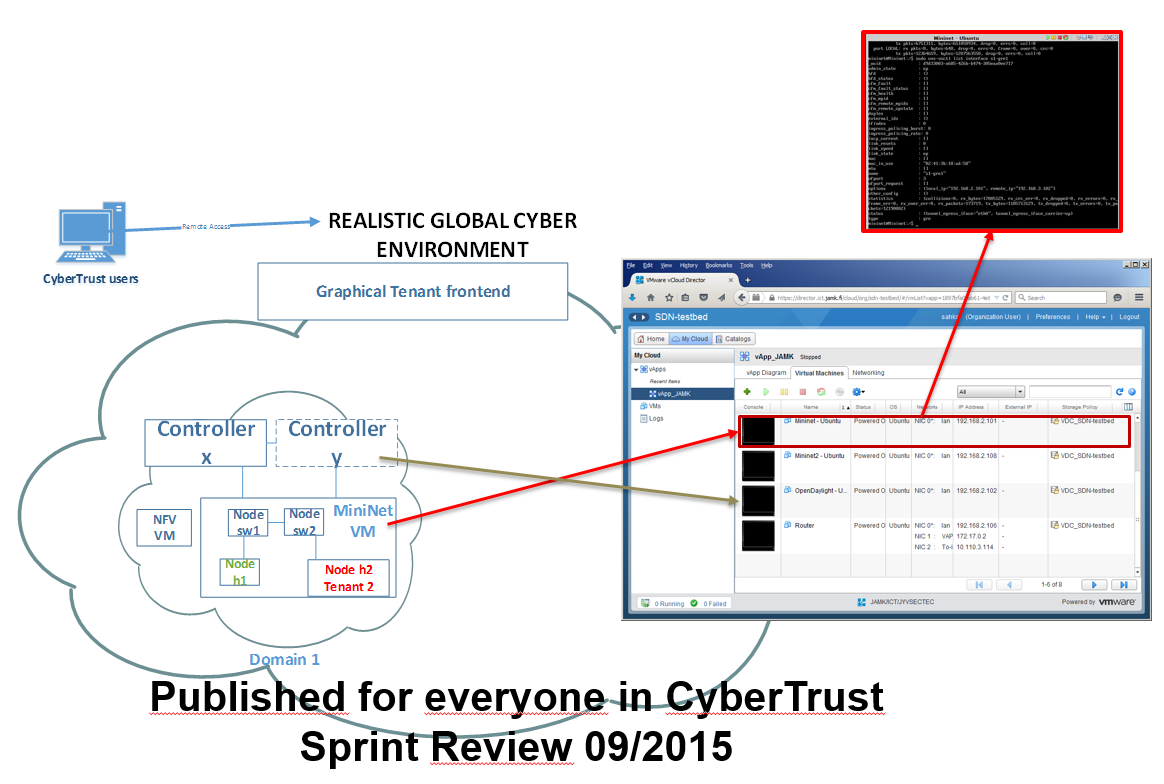
- Goal 1: Implement a SDN testbed based on expected business opportunities with related elements and interfaces for prototyping future systems. Identify missing security components.
Cyber Trust
SDN controlled ISP
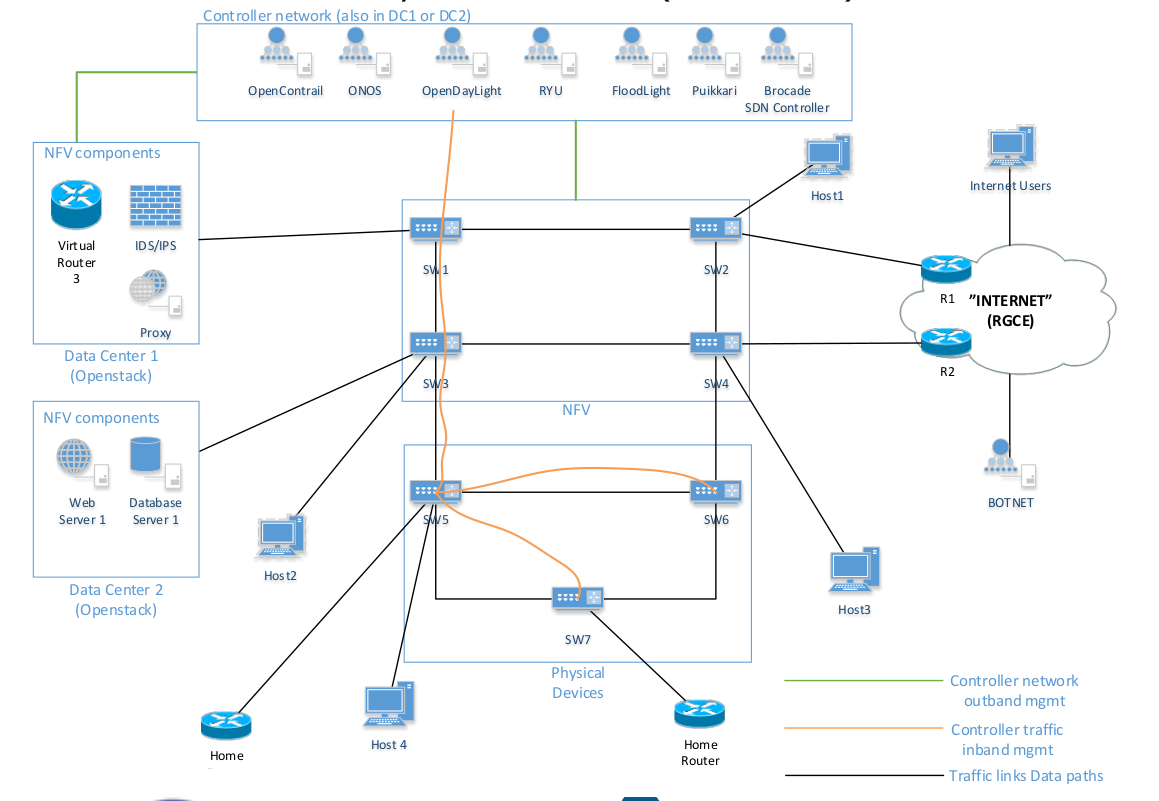
- Goal 3: Study, investigate and identify the cyber threats and attack models and vectors of the selected key architectures (see task 3).
Puikkari
An Orchestration System for SDN and NFV
Puikkari can orchestrate the deployment of Network Functions Virtualization -components and automatically interconnect them in a network utilizing Software-Defined Networks, and visualize them for the user. It also grants the user the control of his/her own network and grants the possibility to add NF services.
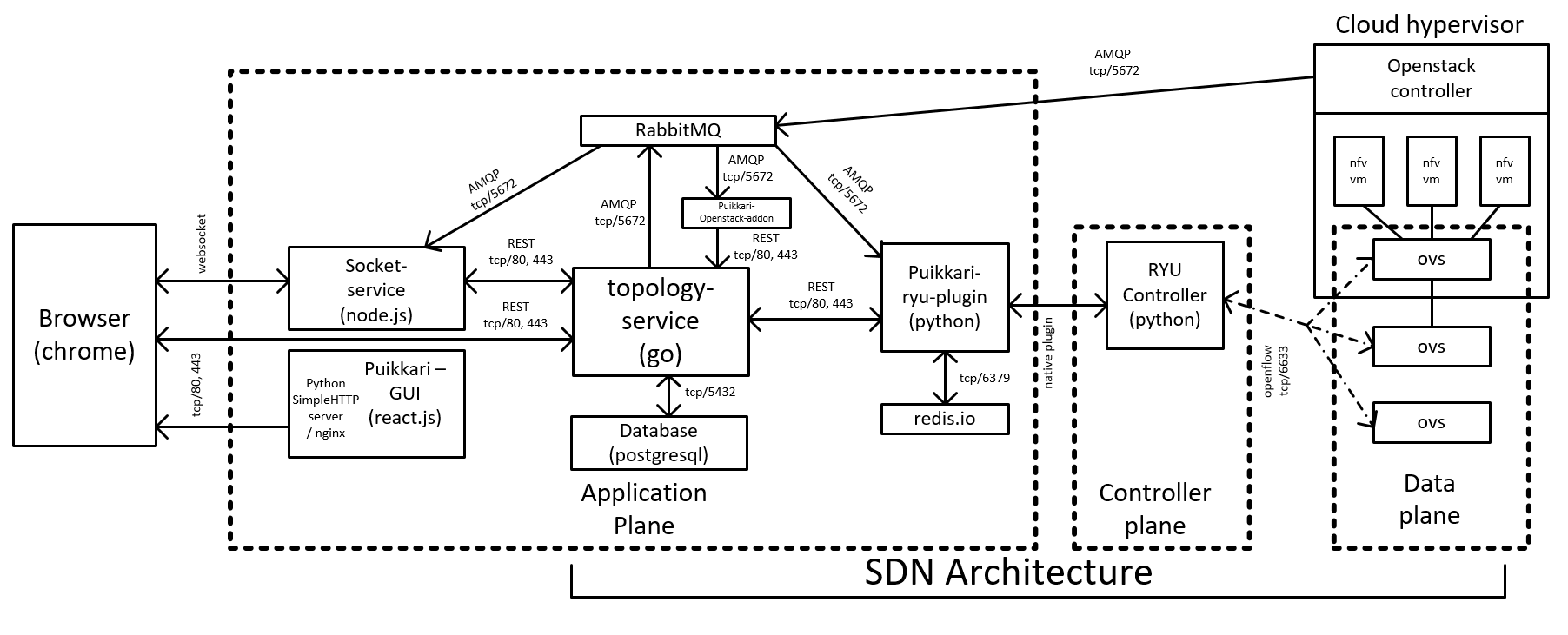
Puikkari
An Orchestration System for SDN and NFV
Puikkari
An Orchestration System for SDN and NFV
Puikkari
An Orchestration System for SDN and NFV
Puikkari
An Orchestration System for SDN and NFV
Puikkari
An Orchestration System for SDN and NFV
Puikkari
Customer buys the Security+ service package from the operator
Puikkari
Network Admin places a customer under monitoring
Puikkari
Customer orders an Advanced Security service
Puikkari
Walled Garden
Cyber Trust
JAMK Personel

- From top left to bottom right:
- Jari Hautamäki
- Karo Saharinen
- Jarmo Viinikanoja
- Marko Vatanen
- Janne Alatalo
- Kaisa Sulasalmi
- Pasi Hyytiäinen
- Ari Salopää
- Juuso Selin
- Henri Tervakoski
- Tuure Valo
- Marko Silokunnas
Thank you!
Check our public repository at: